
Our services
Fractional CISO
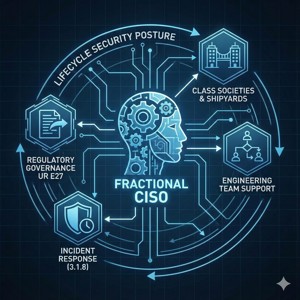
Expert Guidance for Regulatory Governance
Access the strategic insight of a senior security advisor to help navigate complex regulatory demands. Our Fractional CISO service provides guidance on establishing the organisational processes outlined in UR E27, such as the Management of Change Plan (Section 3.1.9) and Incident Response Support documentation (Section 3.1.8). We act as an advisor during interactions with Class Societies and Shipyards, supporting your engineering team in adopting User Identification and Authentication policies (Section 4.1, Req #1) and maintaining a consistent security posture throughout the equipment's lifecycle.
Gap Analysis Audit
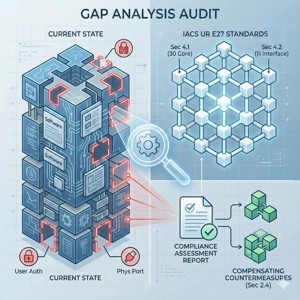
Assess Your Product’s Alignment with Class Requirements
Gain clarity on your product's current standing relative to IACS UR E27 standards. Our Gap Analysis Audit reviews your hardware and software features against the 30 Core Security Capabilities (Section 4.1) and the 11 Additional Interface Capabilities (Section 4.2). We provide a detailed "Compliance Assessment Report" that highlights potential areas of non-conformance—such as gaps in user authentication or physical port protection—and suggests potential Compensating Countermeasures (Section 2.4) to assist you in addressing these findings efficiently.
Document Preparation
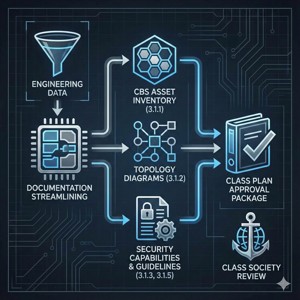
Streamline Your Documentation Process
Reduce the administrative burden of compliance by engaging our team to assist in drafting the documentation required for Class Plan Approval. We work with your engineering data to help prepare essential deliverables, including the CBS Asset Inventory (Section 3.1.1) and Topology Diagrams (Section 3.1.2) used to define vessel security zones. Our services support the creation of the Description of Security Capabilities (Section 3.1.3) and Security Configuration Guidelines (Section 3.1.5), aiming to align your submission with Class Society expectations and facilitate the approval review process.
Vulnerability Assessment in SBOM
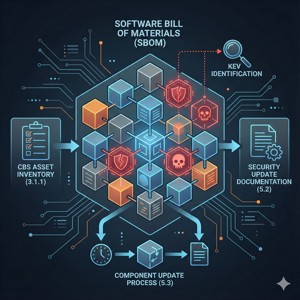
Identify Software Component Risks
Enhance visibility into your software supply chain by identifying known vulnerabilities within third-party components and firmware. This service assists in generating a Software Bill of Materials (SBOM) to support the CBS Asset Inventory requirement (Section 3.1.1) and aids in establishing a Dependent Component Security Update process (Section 5.3). By flagging Known Exploited Vulnerabilities (KEVs) in your operating systems and libraries, we help you prepare the Security Update Documentation (Section 5.2) necessary for Class Society review.
SDL (Secure Development Lifecycle) Gap Analysis
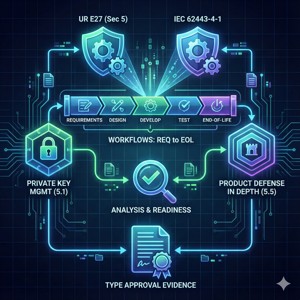
Evaluate Development Process Alignment
Assess your engineering culture against the Secure Development Lifecycle (SDLC) requirements of UR E27 (Section 5) and IEC 62443-4-1. This analysis reviews your current workflows—from requirements analysis to end-of-life—and evaluates your readiness regarding Private Key Management (Section 5.1) and Product Defense in Depth (Section 5.5). We assist in compiling the necessary evidence to demonstrate that security considerations are integrated into your design process, supporting your efforts toward Type Approval.




